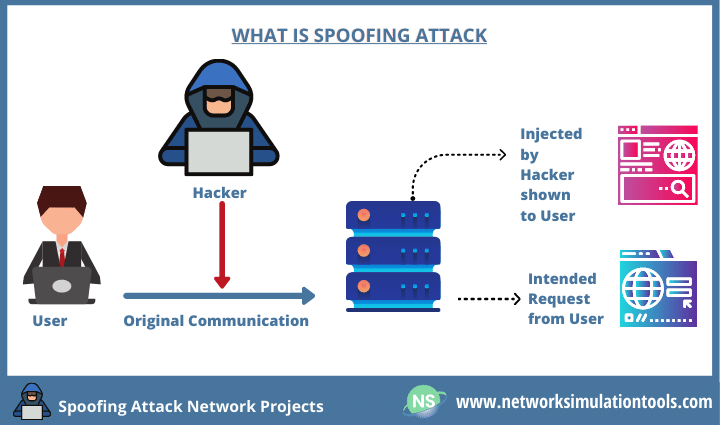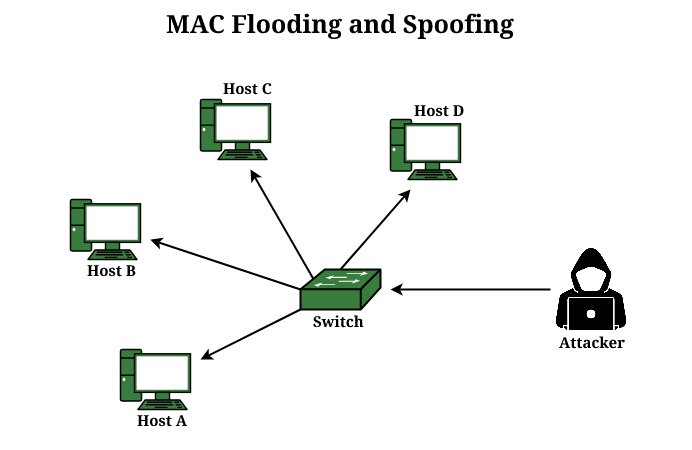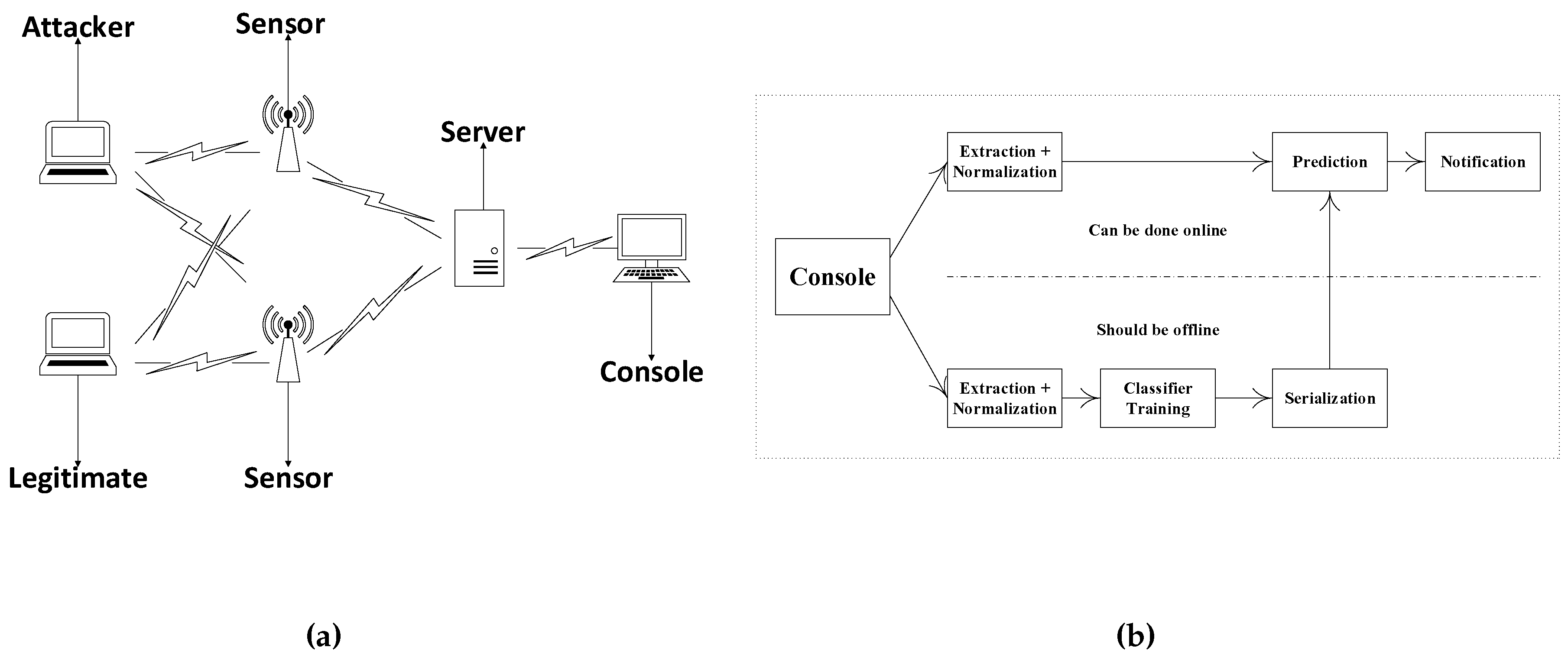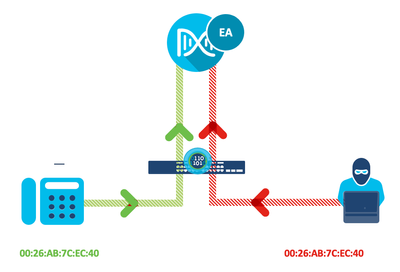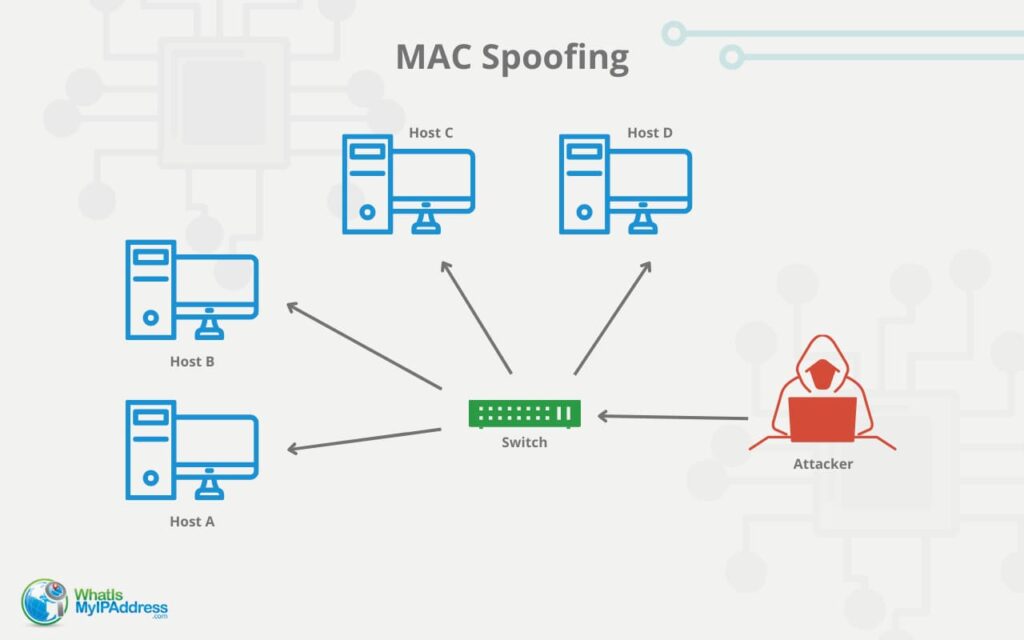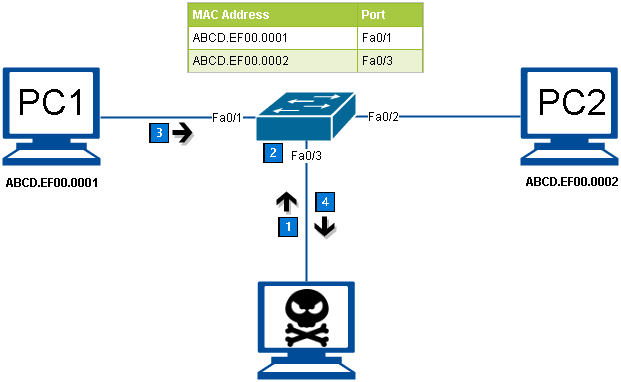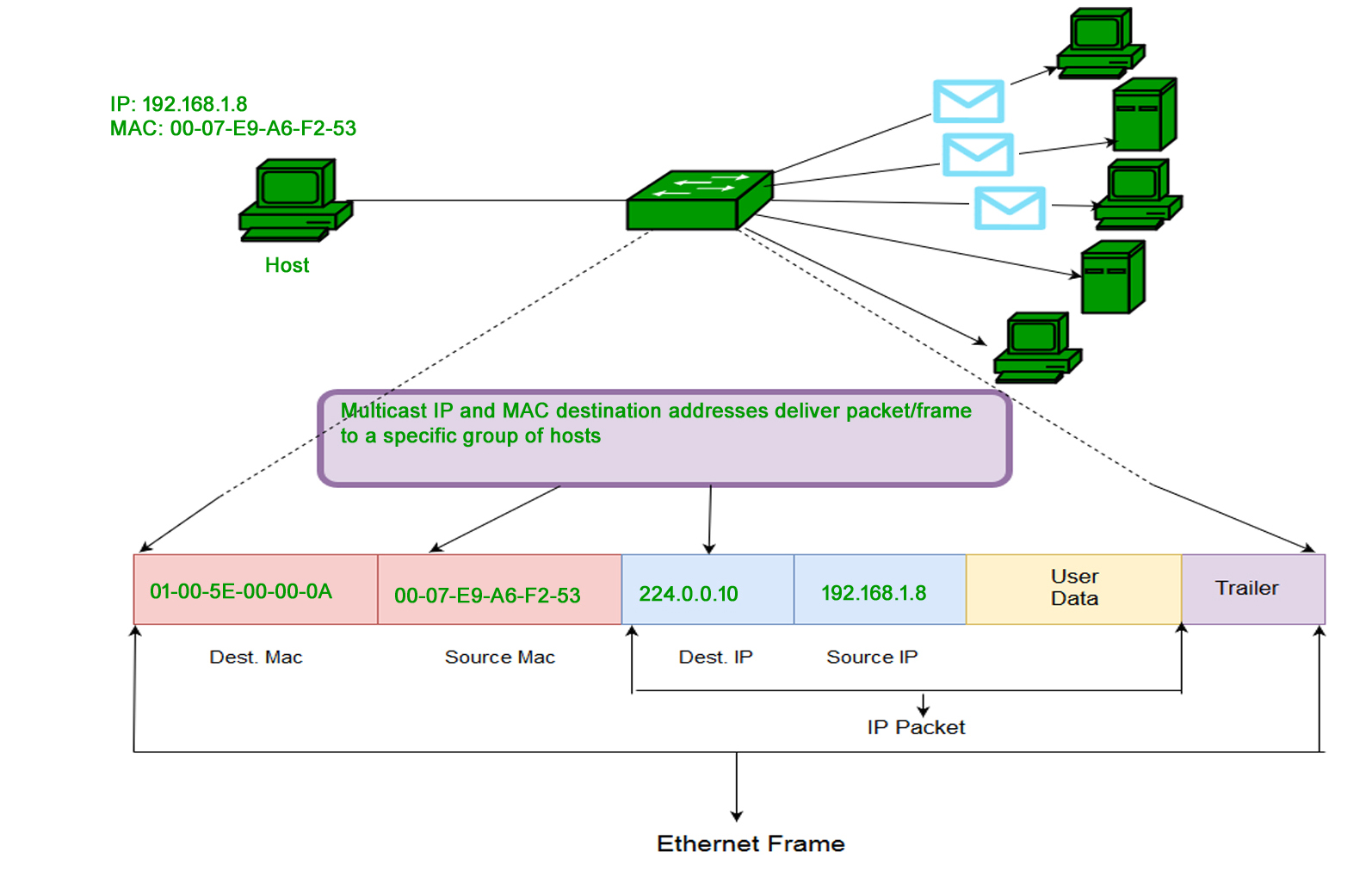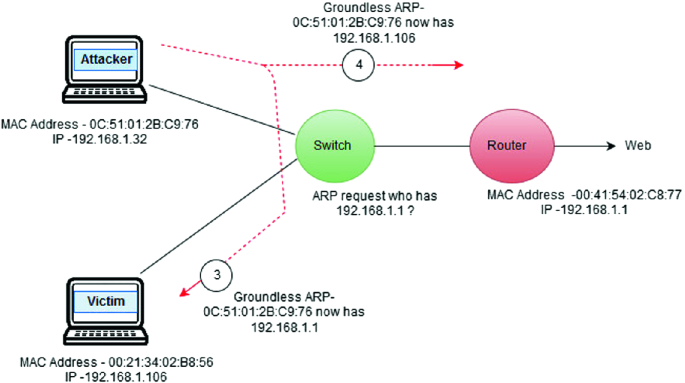
Reliable Monitoring Security System to Prevent MAC Spoofing in Ubiquitous Wireless Network | SpringerLink

StarTech.com Mac Address Passthrough Utility | StarTech.com's Mac Address Passthrough utility helps improve your network security by easily identifying and authorizing devices connected to a docking... | By StarTech.com | Improve your